CI/CD Security Assessment
Evaluate CI/CD Security for a Robust Software Delivery Pipeline Learn More
Continuous Integration and Continuous Deployment (CI/CD) pipelines have become indispensable for organizations aiming to deliver software efficiently and reliably. While CI/CD streamlines development and deployment, it also introduces potential security vulnerabilities.
CI/CD pipelines facilitate the automatic building, testing, and deployment of software. However, without proper security measures, they can unintentionally introduce vulnerabilities. Security breaches in CI/CD pipelines can have far-reaching consequences, including compromised code, data leaks, and reputational damage.
Adversaries, whether highly skilled or less sophisticated, are increasingly focusing on CI/CD systems, recognizing that these services offer an effective route to access an organization’s most valuable assets.
Objective
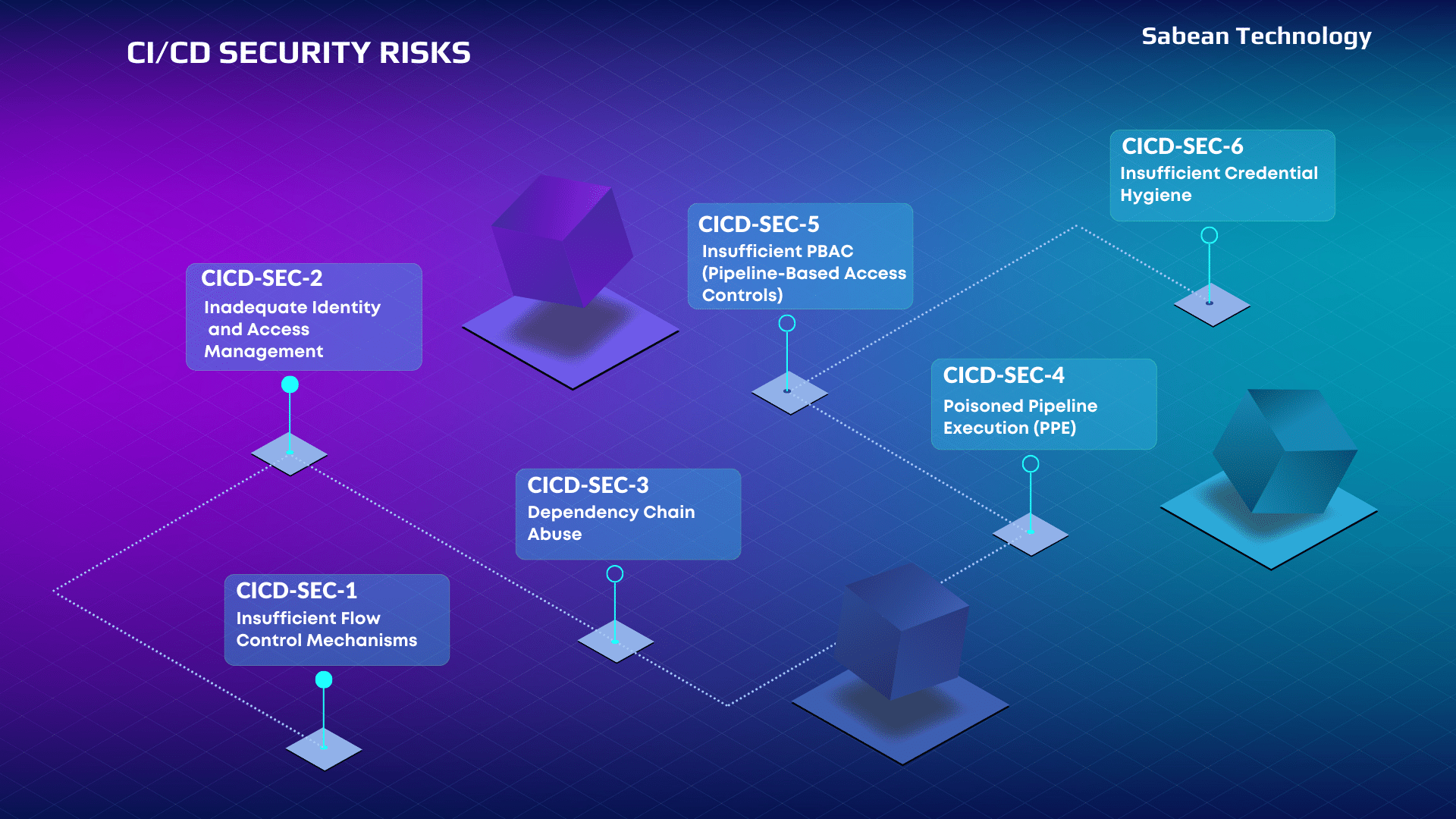
- Identify Vulnerabilities Early: Detect security vulnerabilities and weaknesses in the CI/CD pipeline, application code, and dependencies at the earliest stages of development.
- Mitigate Risks: Prioritize and address security vulnerabilities to reduce the risk of security incidents, data breaches, and other cyber threats.
- Protect Sensitive Data: Ensure the confidentiality, integrity, and availability of sensitive data throughout the CI/CD pipeline.
- Prevent Supply Chain Attacks: Guard against supply chain attacks and ensure that code and components from external sources are verified for security.
Your Title Goes Here
Your content goes here. Edit or remove this text inline or in the module Content settings. You can also style every aspect of this content in the module Design settings and even apply custom CSS to this text in the module Advanced settings.
