API Security Assesment
APIs are crucial components of modern software applications, facilitating communication and data exchange between different systems and services. API security testing aims to ensure that these interfaces are secure and resistant to potential cyber threats.
Secure your API-driven applications with our comprehensive API Security Assessment. Identify vulnerabilities and ensure your digital assets remain protected.
Social Engineering Phishing Simulation
Phishing is a cyberattack method where malicious actors impersonate legitimate entities, often through deceptive emails or messages, to trick individuals into divulging sensitive information like login credentials, financial details, or personal data.
These fraudulent messages may contain links to fake websites or malware. Phishing exploits human psychology and relies on victims’ trust in the sender’s apparent authenticity.
Web Application Security Assesment
A web penetration testing is a specialized cybersecurity service tailored to assess the security of your web applications and web services. We conduct this assessment by simulating real-world cyberattacks to identify vulnerabilities and weaknesses unique to your digital assets.
Our expert ethical hackers systematically analyze your web-based systems, seeking out potential security risks such as coding flaws, configuration errors, and vulnerabilities in authentication and authorization mechanisms.
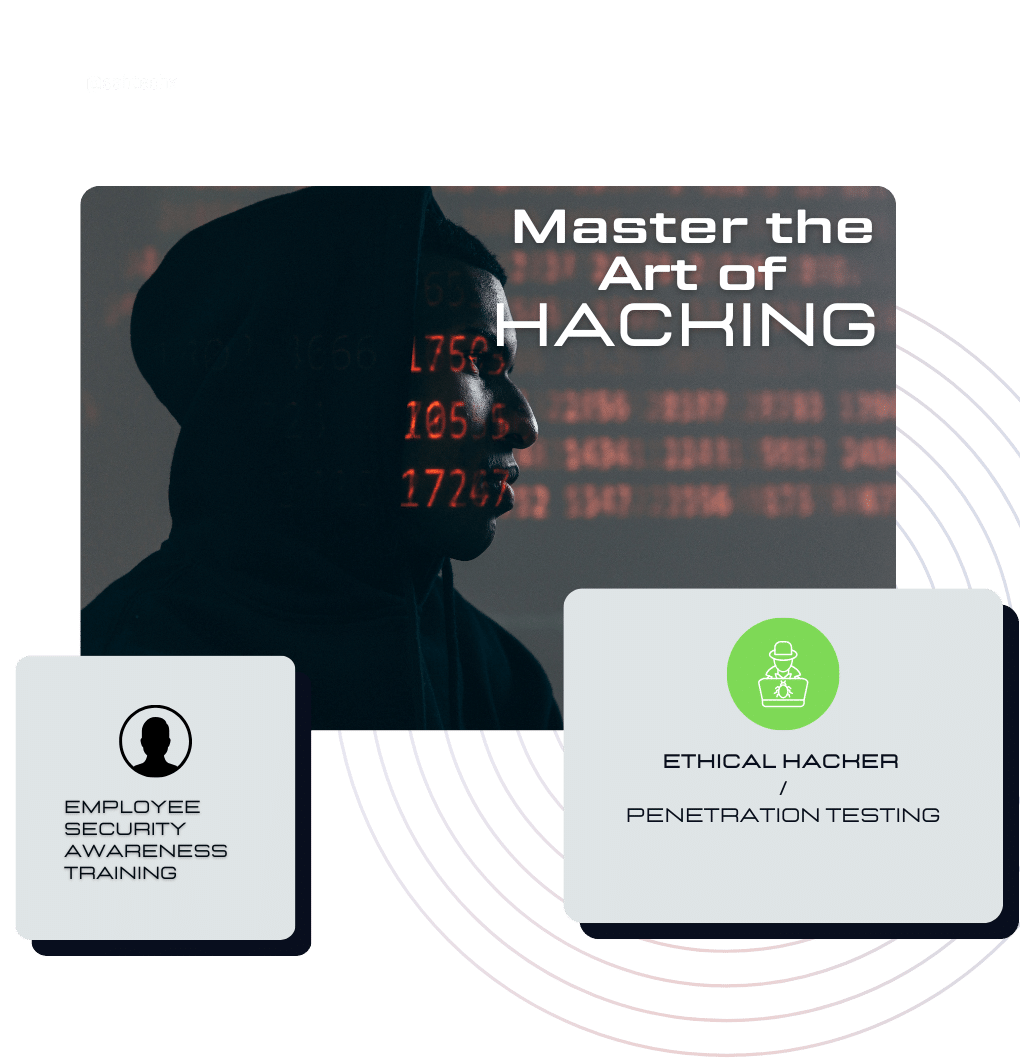
Security Awareness Training
Enhance your security expertise through our specialized penetration testing training. Reach out to us for a stronger cybersecurity foundation.
Empower Your Team with Fundamental Cybersecurity Training (a.k.a Operation Cyber Shield)
Master Ethical Hacking with Our Penetration Testing Course
Tailor-Made Courses to Fit Your Unique Requirements: Order Your Customized Training Today
Red Teaming Adversary Simulation
Elevate your organization’s cybersecurity posture with our Red Teaming service. Uncover vulnerabilities and proactively defend against advanced threats.
Red teaming is a comprehensive, offensive security assessment that goes beyond traditional penetration testing. It involves simulating real-world cyberattacks, using advanced techniques, tactics, and procedures (TTPs) to assess an organization’s security measures.
Mobile Application Security Testing
Ensure the security of your mobile apps with our Mobile Application Security Testing service

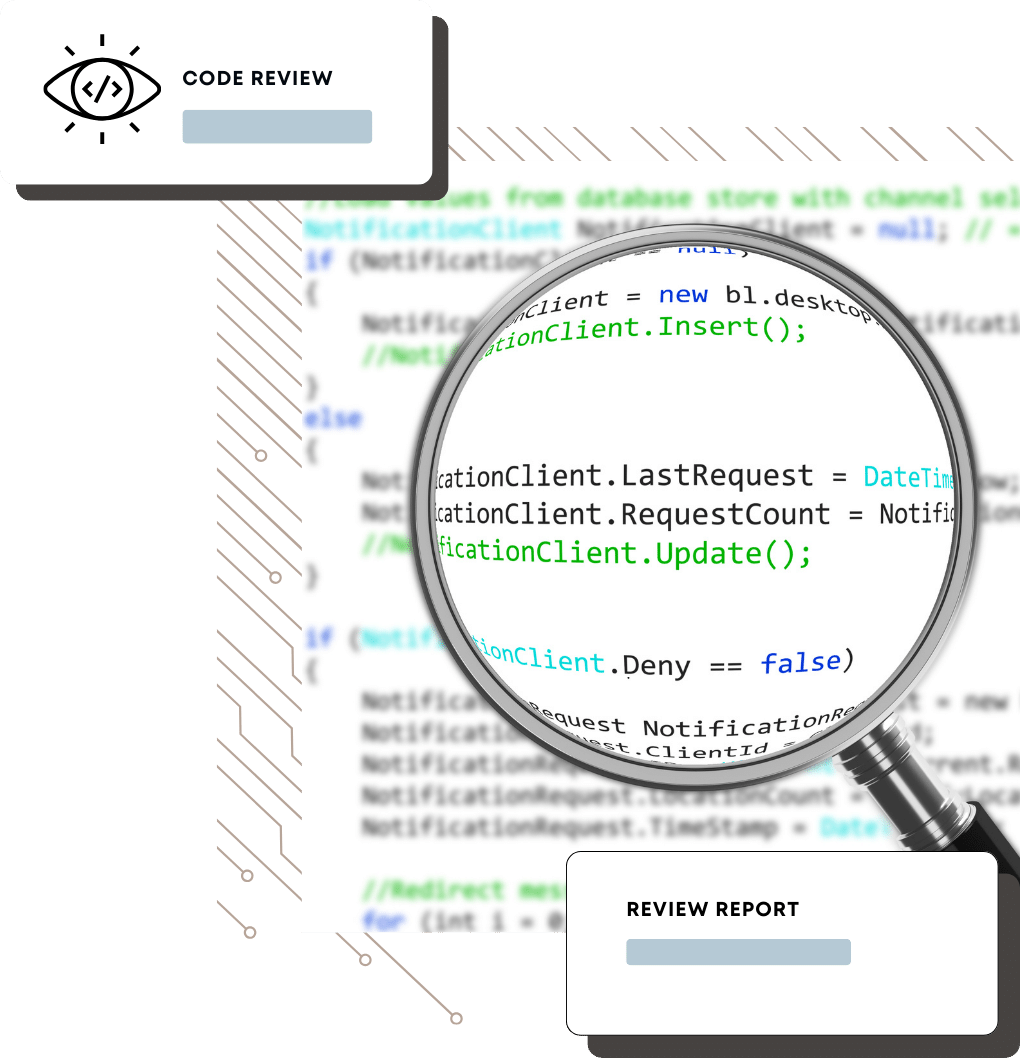
Secure Code Review
A secure code is the foundation of a robust and resilient software ecosystem. Our Secure Code Review Services are designed to help you identify and mitigate vulnerabilities in your software, ensuring that your applications are safeguarded against cyber threats and that your customers’ data remains secure.
Ensure robust application security with our Secure Code Review service. Detect and rectify vulnerabilities early in the development process to safeguard your software.
Threat Modeling
In the ever-changing digital environment of today, cybersecurity threats continually evolve. To effectively identify and counter these threats, a proactive strategy is essential. This is precisely where Sabean Technology’s Threat Modeling Services excel.
Our team of seasoned security professionals is dedicated to assisting you in recognizing, evaluating, and strategizing for potential risks that may affect your organization’s digital assets.


Cloud Security
In the era of cloud computing, organizations are harnessing the power of the cloud to drive innovation and efficiency. However, this digital transformation also comes with its own set of cybersecurity challenges. Protecting sensitive data, maintaining compliance, and ensuring the resilience of cloud-based operations are paramount.
Asses your cloud security posture with our unique Cloud Security Assesment service.
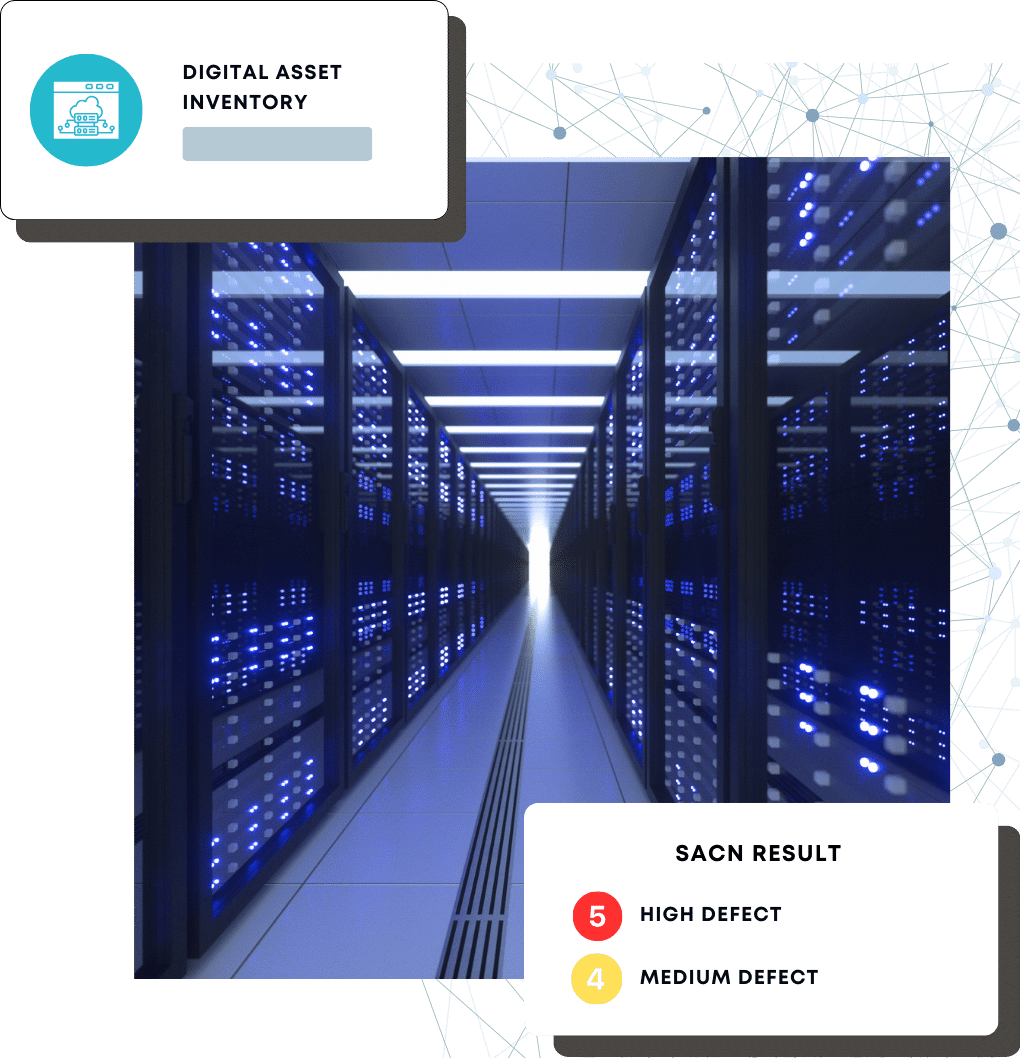
Digital Asset Management
In the digital age, organizations rely on a vast and complex array of digital assets to operate efficiently and effectively. From websites and applications to cloud resources and sensitive data, your digital footprint is ever-expanding.
However, with this expansion comes the challenge of managing and securing these assets. This is where our Digital Asset Discovery Service comes into play.
Discover, safeguard, and optimize your digital assets with our Digital Asset Discovery & Inventory service.
CI/CD Security Assesment
Continuous Integration and Continuous Deployment (CI/CD) pipelines have become indispensable for organizations aiming to deliver software efficiently and reliably. While CI/CD streamlines development and deployment, it also introduces potential security vulnerabilities.
CI/CD pipelines facilitate the automatic building, testing, and deployment of software. However, without proper security measures, they can unintentionally introduce vulnerabilities.
